In this post, I show how to configure ClearPass SSO with Azure AD. I use SSO (single sign-on) to authenticate operators, using ClearPass. To use SSO for users to authenticate against the network and onboard new devices, for example, will be a later post.
What and Why?
So what is SSO or single sign-on? Actually this is nothing new nor something special. Most of today’s organizations use some kind of single sing-on. And if your organization does, it totally makes sense to integrate ClearPass into the SSO system.
A SSO system allows the user to sign-on once and use all the applications and/or websites without reauthenticate again. If you like to access an application, the authentication is done in the background and you have a seamless and uninterrupted workflow.
You can have your own SSO system or you can use one of the cloud-based systems like Azure or Google Apps, just to name the two of them. Even ClearPass itself can be a SSO system.
So why should I use such a system? The answer might not be the obvious one but it could make your system more secure. And here is the reason. First, the application or web page will never see your credentials. They will only get a response from the SSO system if the user is permitted or denied.
Secondly, your users will see only one page where they need to enter their credentials. This is the SSO page. Every other page, asking for credentials should be treated as an attack. From my point of view, even someone without any IT knowledge can follow this rule.
For this post, I will use ClearPass SSO with Azure AD, which uses SAML in the background to exchange the authentication data.
I will not go into the details of SAML and assume you know what we are talking about. If not, have a look here:
https://en.wikipedia.org/wiki/Security_Assertion_Markup_Language
The Azure AD Part
Let’s start with Azure. Unfortunately, I do not have a premium subscription for Azure, so I need to work with the free version. (Maybe someone at MS can help me out 😜)
Why do I’m telling you this? If you have a premium subscription, you can build your own SSO app. With the free version, this is not possible. But you can use existing apps and reuse them for ClearPass. The following part is about this reuse thing. If you need to know, how to build your own app, have a look at the official Aruba document here:
To use an existing app and modify it for ClearPass read on. I assume you have a running Azure AD and you know how to work with Azure AD. To add a new app, select your directory and go to “Enterprise applications”:
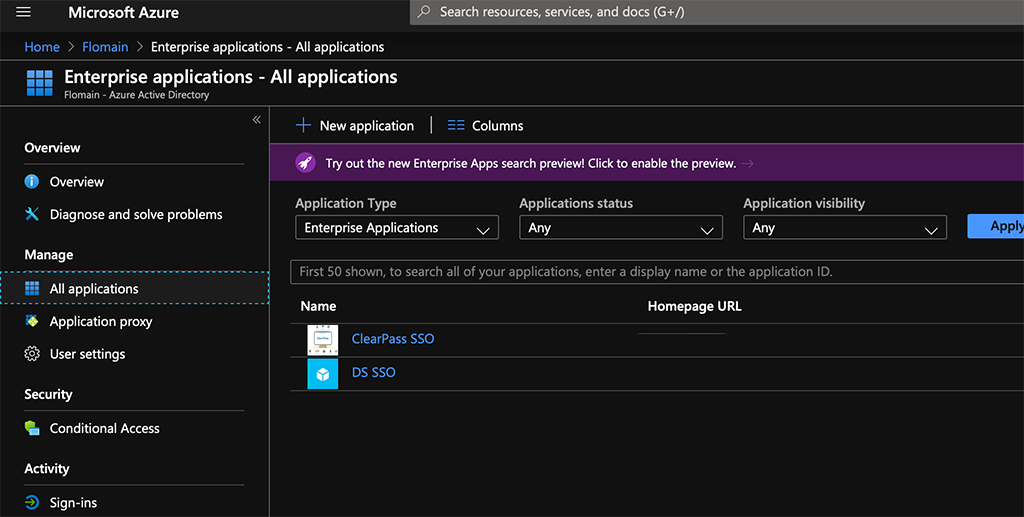
Here you can hit the “New application” button and search for “KnowBe4” and select the entry:
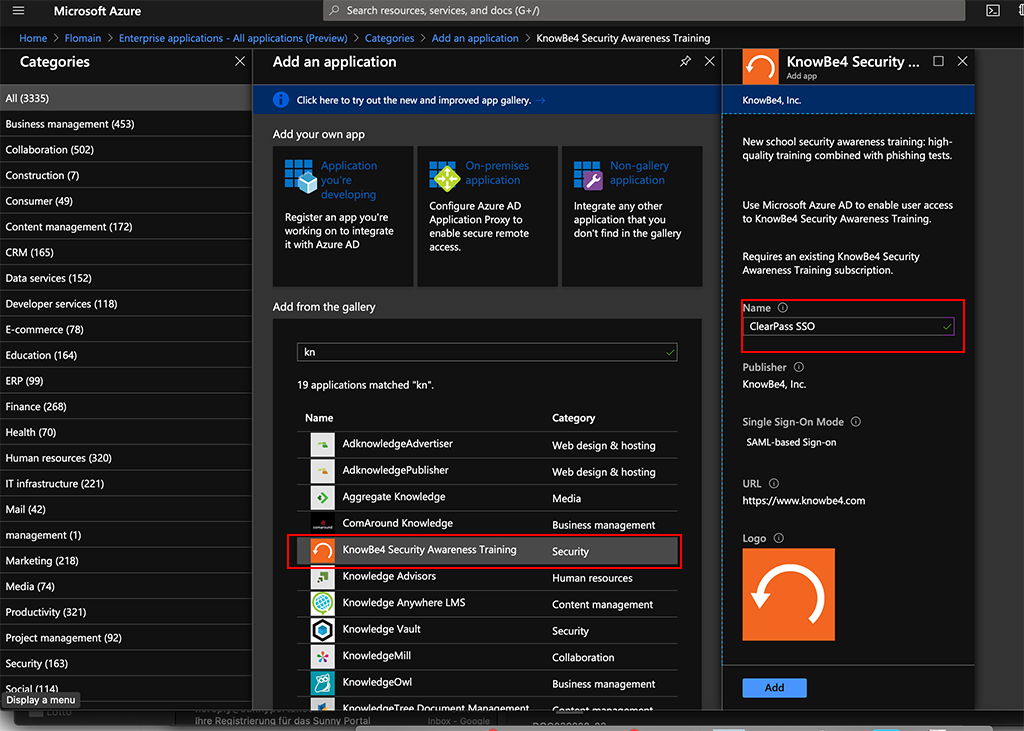
Add a name for the app and click the “Add” button. Then wait for Azure to finish the task.
After the app is available your browser will be redirected to the app page. From there navigate to “Single sign-on”:
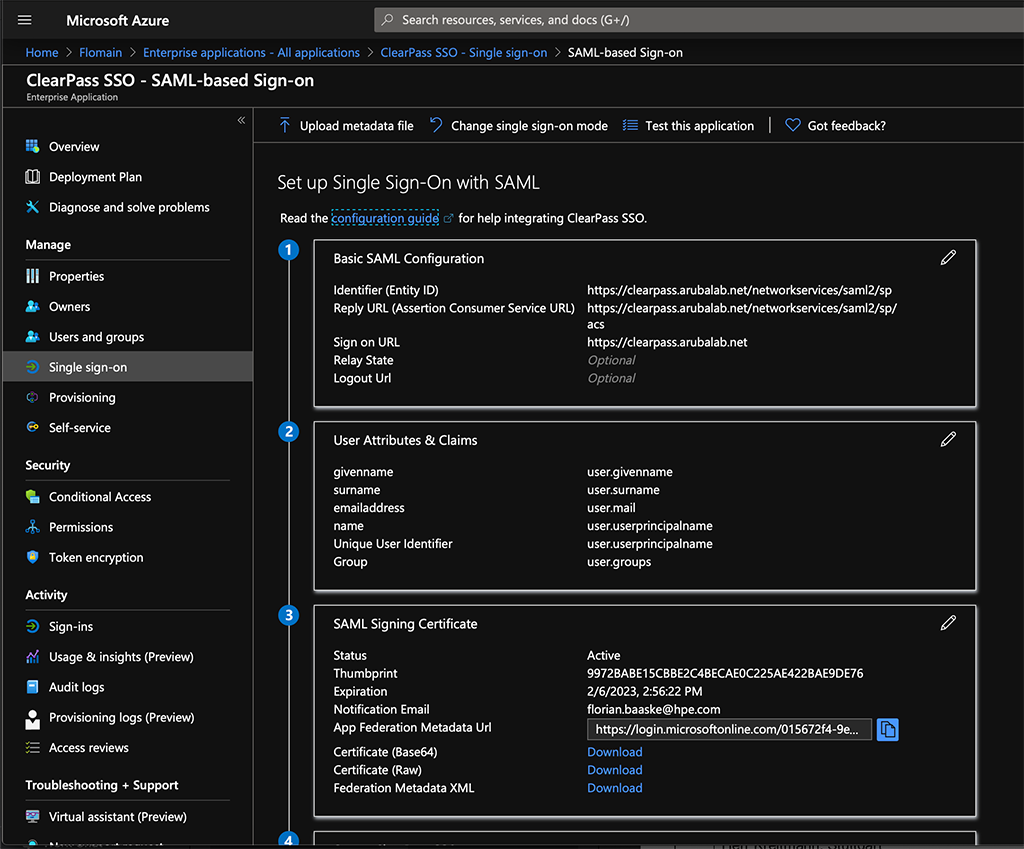
Now, you need to modify or add the configuration. The first part is “Basic SAML Configuration”. Here you need to insert the entries from the screenshot above. The “Identifier (Entity ID)” should look like this:
https://<clearpass-fqdn>/networkservices/saml2/sp
The “Reply URL (Assertion Consumer Service URL)” like this:
https://<clearpass-fqdn>/networkservices/saml2/sp/acs
For the “Sign on URL”, I use the ClearPass FQDN as well, without anything behind it. The reason is, that the request might come from different pages like the policy manager login page or the Insight login page. Depending on which service is enabled for SSO.
Afterward, you can change or add “User Attributes & Claims”. For my setup, I added the “Group” claim. This allows later to differentiate between users who access ClearPass and give them different Access levels.
The very last step is to download the “Certificate (Base64)”. We need this for ClearPass. You also need to copy the “Login URL” for this application:
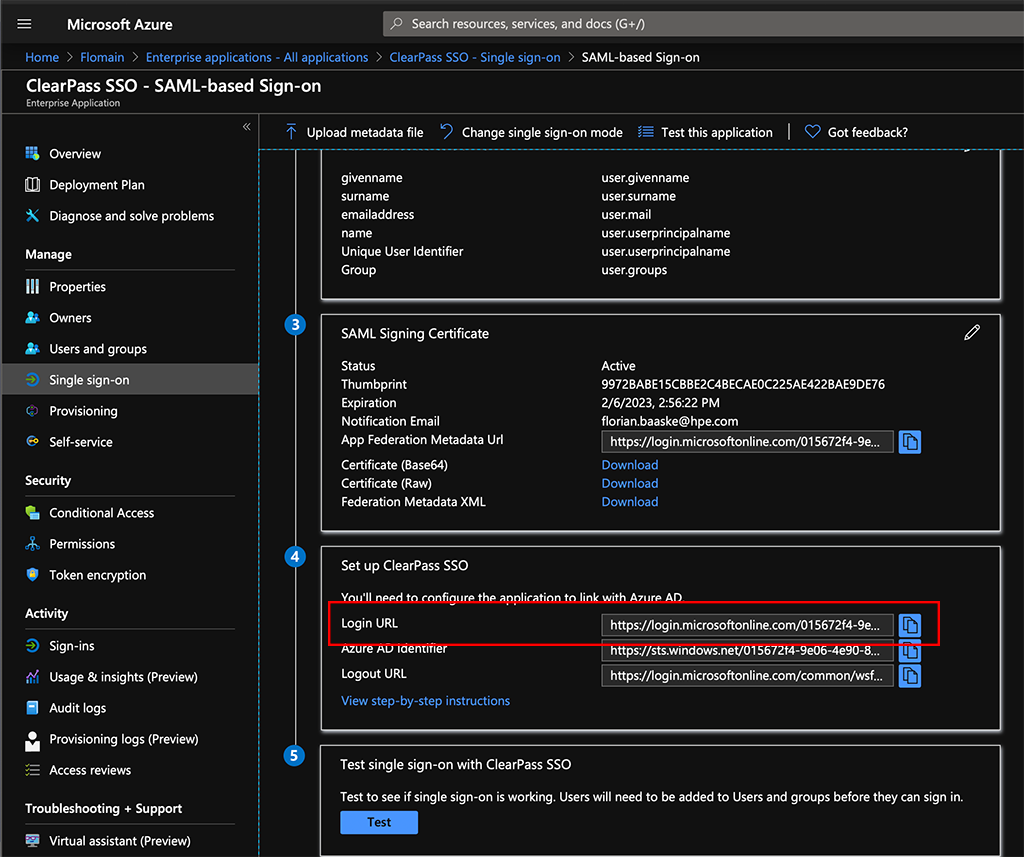
You can now assign users or groups to this application by going to “Users and groups”. This is very self-explanatory.
ClearPass SSO with Azure AD
Now we head over to ClearPass. The first step is to import the downloaded certificate into the ClearPass “Trust List”. To do so, go to “Administration–>Certificates–>Trust List” and use the “Add” Button:
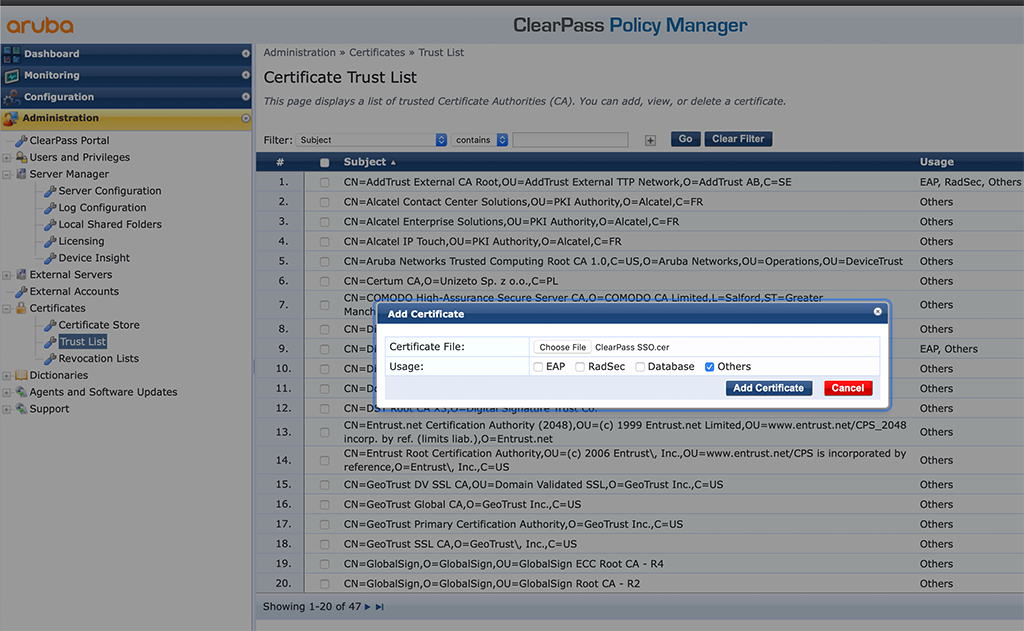
This adds a new self-signed certificate to your “Trust List”. The “Subject DN” of this cert is:
CN=Microsoft Azure Federated SSO Certificate
This certificate is used by Azure to sign the answer from Azure. So ClearPass can be sure, that the answer is correct and from a trusted source.
The next step is to enable SSO for ClearPass. Go to “Configuration–>Identity–>Single Sign-On (SSO)”:
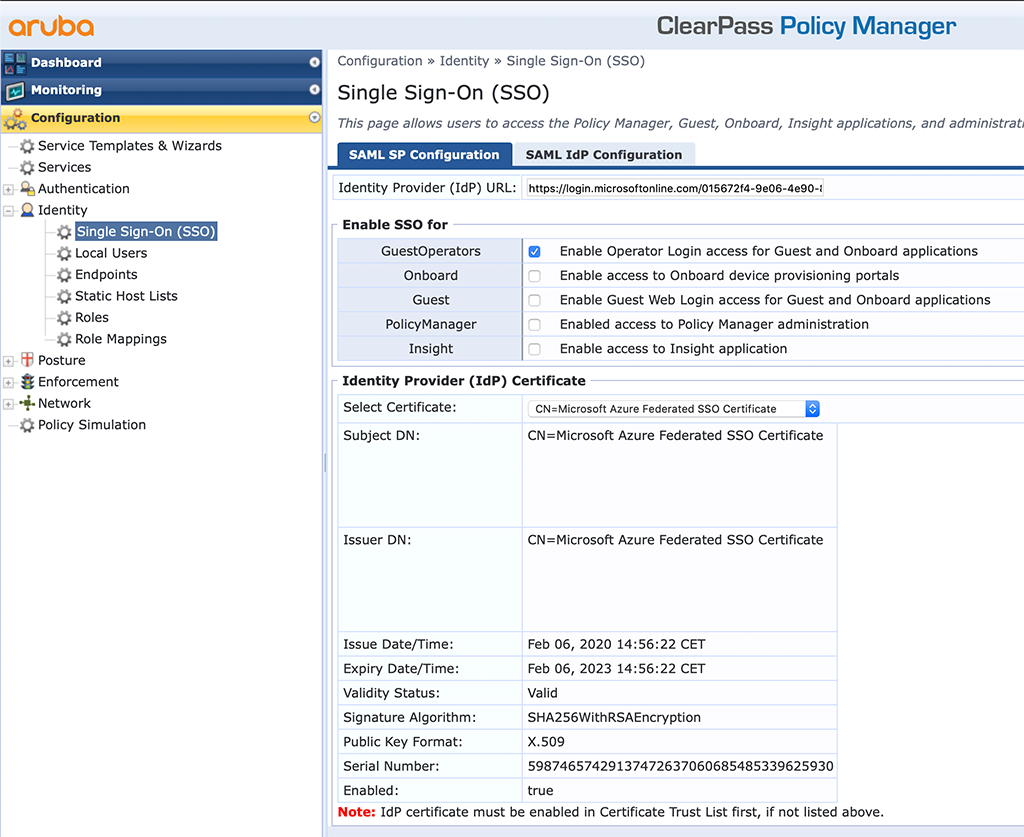
Here you need to make some changes. The above is already the finished picture. First, enter the “Identity Provider (IdP) URL”. This is the “Login URL” from the Azure part above. For a first try, I would enable SSO just for one application within ClearPass. I started with the guest and onboard part. You can also try with a different app. But then, all the following descriptions need tp adapt.
In the “Identity Provider (IdP) Certificate” section you select the imported certificate from Azure. without the correct certificate, the authentication will fail.
The last step is to save the configuration. You now have a basic ClearPass SSO config.
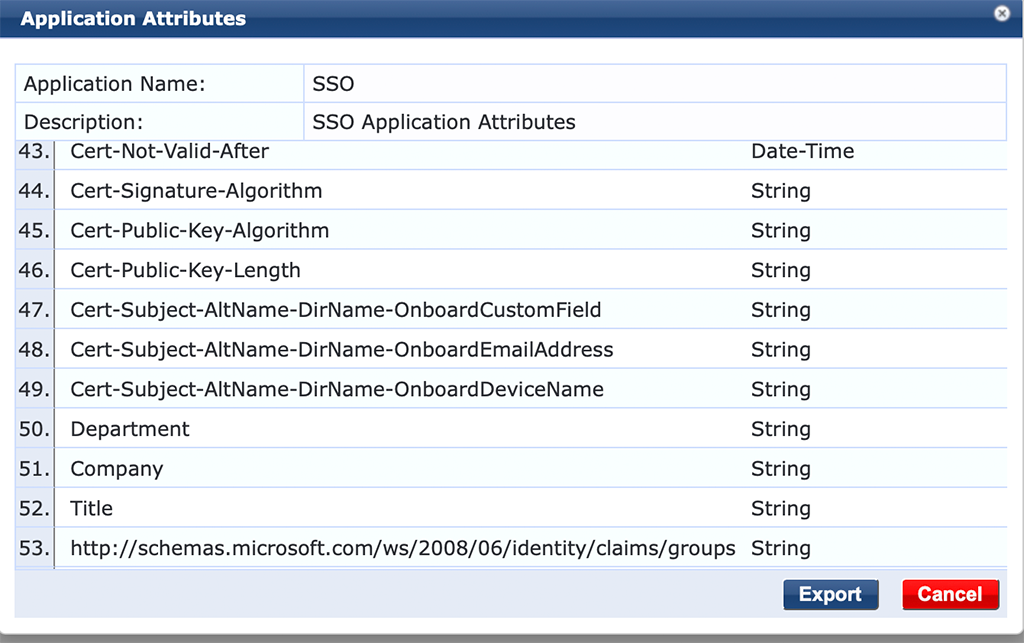
During the config of Azure, I added the group claim. Unfortunately, this attribute is not known by ClearPass. So you need to add this to the application dictionary. If you do not need to assign different roles to users, based on Azure groups you can skip this step.
If you need different roles, read ahead. Go to “Administration–>Dictionaries–>Applications” and select the “SSO” dictionary. You can export the dictionary with a click of the “Export” button in the lower part of the new window.
Add the following line to the file:
<ApplDictionaryAttributes attrType="String" attrName="http://schemas.microsoft.com/ws/2008/06/identity/claims/groups"/>
Save the file and import the file again. The “SSO” dictionary should look like this:
Create SSO Services
The last part is to create a service to use the data from Azure for authentication. I will not go through every step, as I assume you know how to create Services, Role Mappings, Roles, Enforcement Profiles and Enforcement Policies in ClearPass.
Below is the Service to authenticate guest and onboard operators:
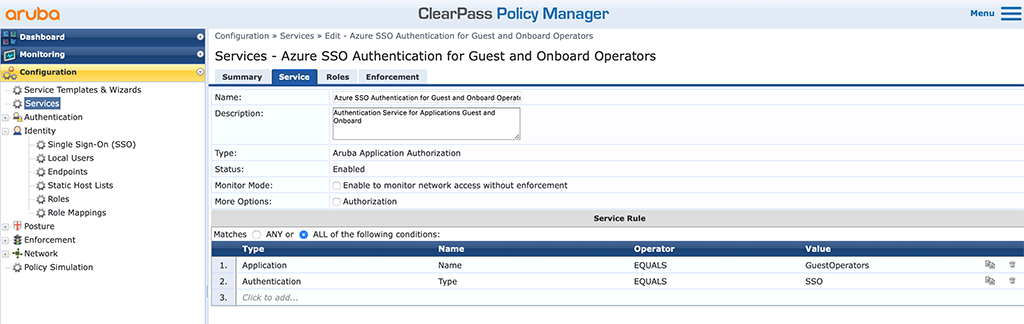
The “Type” of the service is “Aruba Application Authorization”. “Service Rules” are very simple. I use the “Application” “Name”, in this case, “GuestOperators”, and “Authentication” “Type” is “SSO”. Both conditions must be true in order to use this service.
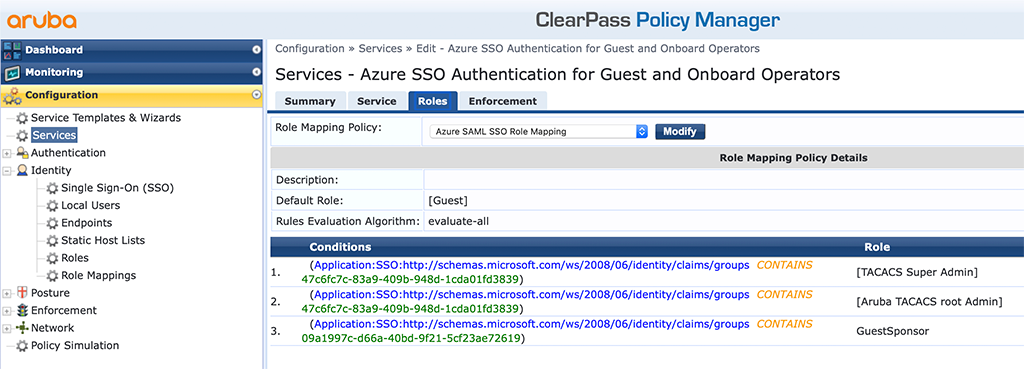
To make my life easier, I use a simple “Role Mapping Policy”, which converts the cryptic Azure roles (you will only get the “Object Id” from Azure) into roles on ClearPass. This is something you can do and I recommend it to do, not only in this case, but it is completely up to you.
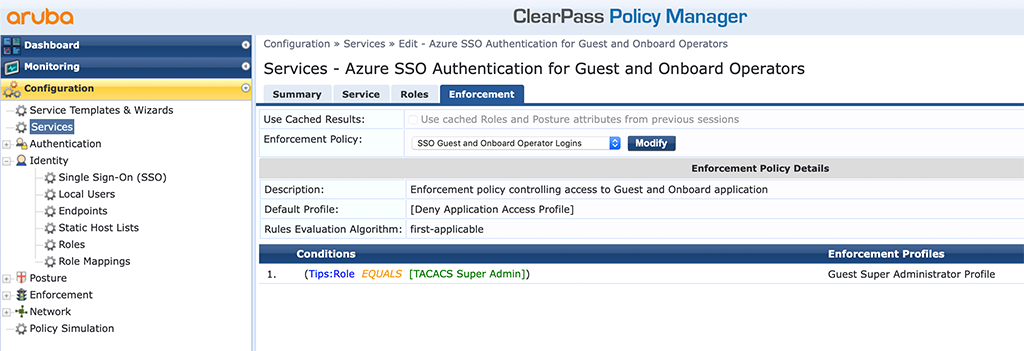
The “Enforcement” is very simple as well. At the moment, it is just me using ClearPass, so I simply enforce the “Super Administrator”. If you need more granular profiles, like profiles for receptionists or sponsors or whatever you need, just add more conditions to your enforcement policy.
As the enforcement profile and the enforcement policy looks different than for normal TACACS+ authentication, as described here, I will show my profile and policy in detail.
First, the enforcement profile:
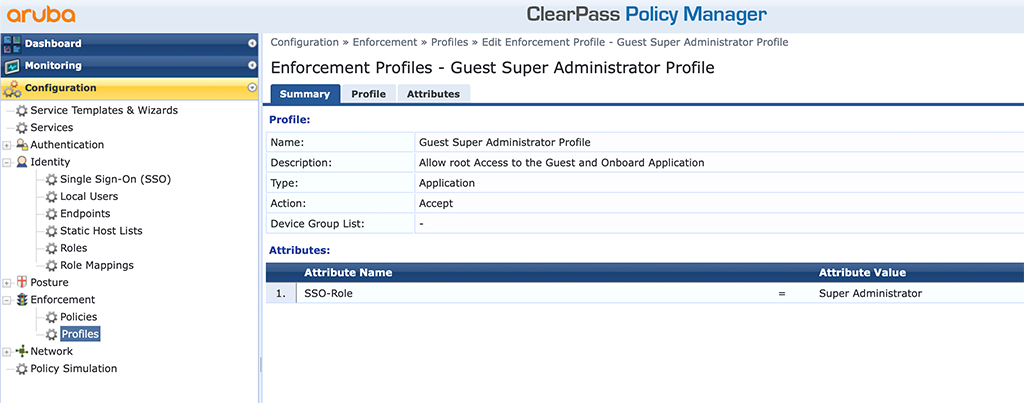
The profile is from “Type” “Application” and you return the “Super Administrator” role as a “SSO-Role”.
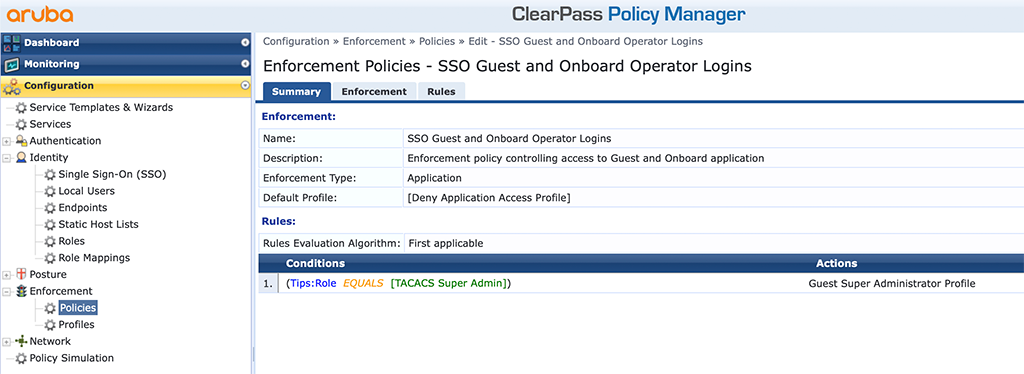
The policy is as well an “Application” “Enforcement Type”. The conditions are configured the same way as for all other policies. BTW: don’t blame me for using the “TACACS Super Admin” role within ClearPass. I just reuse what is already there. For your system, you should create your own roles instead of using the default ones.
After everything is ready you can try to login to the guest application. You should be redirected to the Azure login page to provide your Azure AD credentials. Afterward, you should be authenticated within the guest application.
The policy manager “Access Tracker” should have an entry for you like this:
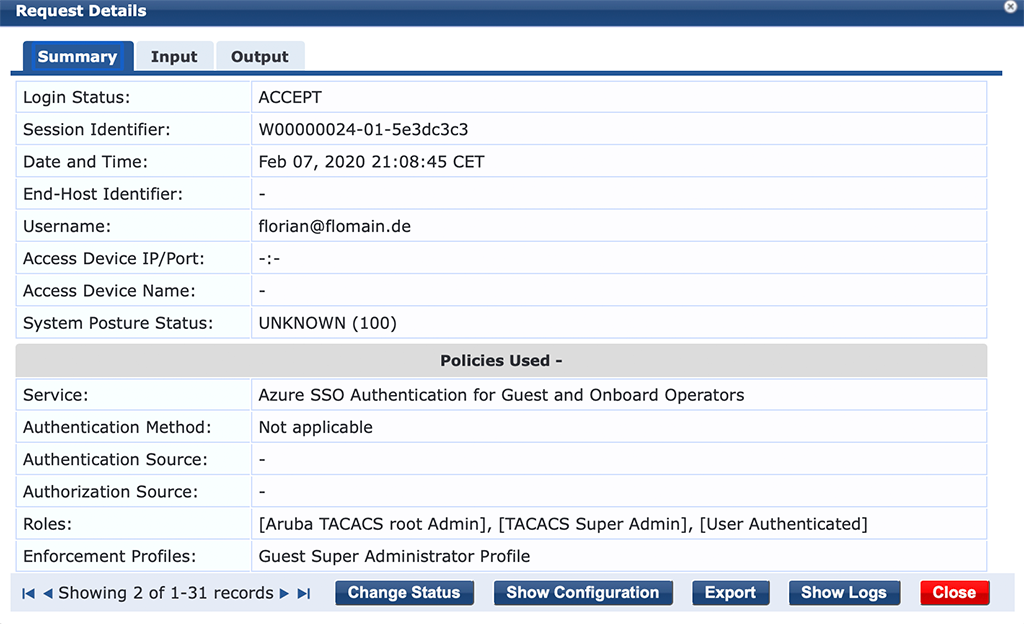
Nothing special here, but have a look at the next tab:
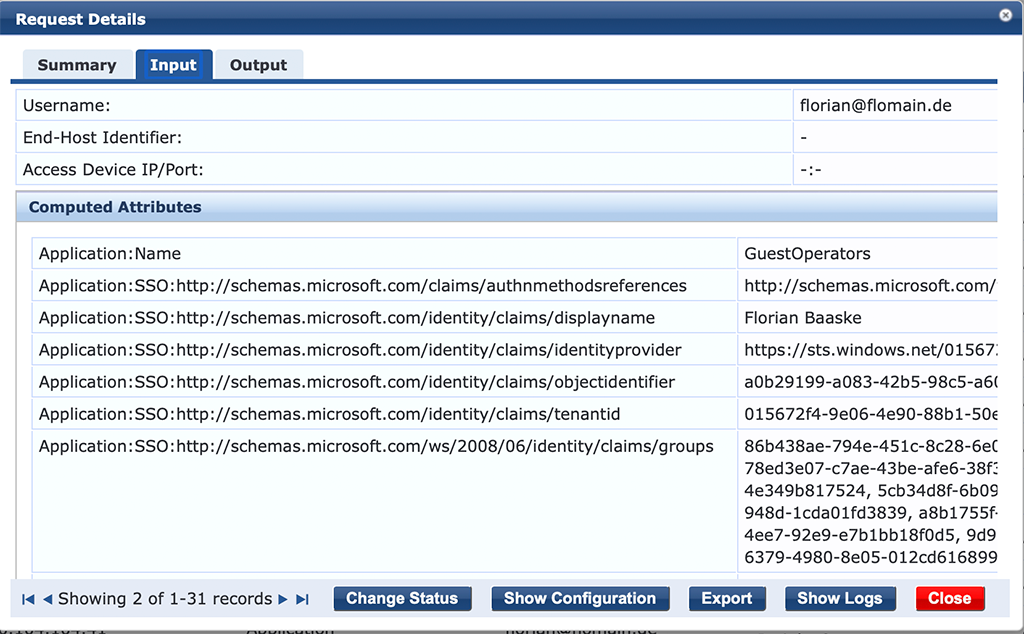
You see all the attributes coming from Azure.
You might now start to enable SSO for other application parts in ClearPass like Insight or the Policy Manager itself. I have all of the applications in ClearPass SSO enabled.
If you find this post useful, leave me a comment and share your feedback with me. You can also buy me Pizza, using the “Buy me a Pizza” button on the right, to support this blog and keep the IT gremlin happy.
If you would like to do me a favor, share this post with your friends and social media contacts. This would really help to make this blog more popular and help others to find the information above more easily using search engines.
Share on:
Great write up. I implemented this myself but also incorporated Azure App Proxy so I could make a guest operator page available for students to whitelist their IoT devices.
Hi Ryan,
Thanks for the comment, I really appreciate your feedback.
You are correct, there are plenty of options with Azure and this was just some kind of introduction to show how simple it is to use something like Azure AD.
Many thanks,
Florian
Really like your blog! im going to test some of these out to see if this works with TACACS authentication on network devices login. I hope you keep writing in the future!
Hi Bas,
thanks for your comment. I really appreciate your word.
To your question, unfortunately, you cannot combine Azure SSO with TACACS+. TACACS+ does need a user password combination, entered at the device login prompt. You cannot pass this to Azure.
BR
Florian
Thanks for this write up. Just to let you know that there is a small typo in your URLs that will lead to an AADSTS700016 error when the user tries to log in. It must be networkservices not networkservice. It is correct in the screenshot.
Hi,
thanks for the feedback. Really appreciated.
Must have overseen the typo and corrected the typo. Thanks for letting me know.
BR
Florian
Hi, thanks for the great post!
I’m trying to get this setup for our MPSK device registration. We have our 4 Clearpass servers behind our F5 load balancer and when I go to the initial site that we will be publishing on the load balancer and then log in with O365, it redirects me back to the originating Clearpass server and not to the load balanced site.
Do you know how I could send the correct reply URL to O365? We do not want users accesing the Clearpass servers directly. Also, I had to add in all my 4 Clearpass servers on the Azure portal or else I was getting an error.
We are currently running Clearpass 6.8.5
hi,
I saw the same. I’m running two ClearPass servers and access them via the VIP, but after authenticating, I’m always redirected to a specific IP instead of the VIP. I was not looking into this, as it still suits my needs, but let me check if I can get something on this.
BR
Florian
Is there anyway to use this setup to authenticate guest users via captive portal to permit internet access? Very similar to the self registration guest setup but use Azure SSO to authenticate?
Hi Jeremy,
Sure this is possible as well. Have a look at this document:
https://community.arubanetworks.com/community-home/digestviewer/viewthread?MID=18612
Hope this helps. If not, leave me a reply and I will try to write something up. But it could take a while as I have some other stuff I need to prepare first.
BR
Florian
Hi Florian,
First of all thanks for this, and all the other, articles on your blog. I found them very useful and nicely laid out. Keep on going :-).
One question though, the link for “ClearPass_Configuration-Guide_Onboard-Cloud-Identity-Providers_v2018-01.pdf” document is leading to the old ASP portal, that is not in use anymore. Do you know where can document be found (I tried in the new ASP, but couldn’t find it)? Thanks
Hi NesaM,
Thanks for the hint. Actually, it is on ASP. You can find it here:
https://asp.arubanetworks.com/downloads/documents/RmlsZTo0NDZlZmM1NC1lNmZiLTExZWEtYjE5OC04Nzc5YzY0NjgwOGY%3D
I will also update the link in the post.
Many thanks,
Florian
Hello Florian,
Great article, but I am curious if you have the same “issue” with SSO as I have. I configured the SSO part in Azure and ClearPass and when I browse to the GuestOperator page, CPPM redirect me and I can enter my credentials including MFA, so far so good.
The “problem” I am having: we have more sites using SAML with SSO against Azure, like portal..com and self-service..com. When I log into one of them, I need to authenticate. When I go to the other site, I don’t need to enter my credentials, but SSO logs me in. But when I browse to the GuestOperator I need to enter my credentials again, so “real” SSO doesn’t seem to work.
Hi René,
I found the same. Need to reauth every time I connect to CPPM even if the session should still be valid. This came with the upgrade to 6.9 last year. But no one I know had the same issue so I was thinking this was simething with my setup.
I would suggest to open a Case with Aruba, as this is not how it should work.
BR
Florian
Hello
Sir … I am following Your blog for very long time.
Great work and mostly of all very helpful content.
I have a question, because I am stuck with OnBoard and Azure AD … is any chance to drop You an email?
BR
#MJ
Hi Milosz,
Sure, you can drop me a mail. But keep in mind that this is on a best-effort basis. you can also ask your questions in the Aruba Community here:
https://community.arubanetworks.com/community-home?CommunityKey=2477474f-de43-4598-a465-c179d41fdd0b
BR
Florian
Hi Florian,
I have configured SSO with Azure and trying to Onboard Android clients using Quick-Connect application but it give an error “Invalid Single sign-on Token (E1).
any idea on this issue.
Hi,
I haven’t seen the issue so far, but if you to a packet capture, you could check the SAML information by yourself and check if everything is correct. The messages sound like something is not correct configured.
BR
Florian
Hi, How can we manage the failover with SSO in a environment with Publisher and Subscriber.
Hi Harendra,
Thanks for the question. What do you mean if you say failover?
If you follow my post the login to all members of the cluster should work with SSO, even in a situation where the publisher is not available.
BR
Florian
In the place where you mentioned “To make my life easier, I use a simple “Role Mapping Policy”, which converts the cryptic Azure roles (you will only get the “Object Id” from Azure) into roles on ClearPass. This is something you can do and I recommend it to do, not only in this case, but it is completely up to you.”, I not not sure how you added the conditions under the roles tab in the services
could you please tell that
Hi Srivathsan,
thanks for your comment.
I’m actually not 100% sure that I got your question correctly. If you need help to create a role mapping policy, please take a look into the documentation:
https://www.arubanetworks.com/techdocs/ClearPass/6.11/PolicyManager/Content/CPPM_UserGuide/identity/RoleMappingPolicies.html
If you are asking where I got the attributes from, this is a different story.
The condition is from the SSO Dictionary. How to add the Azure specific parts to the ClearPass SSO Dictionary, is described in the article above. Somewhere in the middle, just before the “Create SSO Services” headline.
The value from the condition is the object id of the group in azure.
If you follow the article, you should get everything correct. If you still encounter problems plese let me know.
BR
Florian
Hi Florian,
Very informative blog. How can we integrate multiple network security vendors with ClearPass for SAML integration. I want to configure a customized guest page(s) for multiple vendors like Palo Alto and Fortinet and login using SAML.
Hi Umair,
Thanks for you question, but it is not really clear for me what you would like to achieve. The best way would be to contact you aruba PreSales contacts or your partner to work with them on a solution.
BR
Florian
Hi Florian,
Could you please share any steps to integrate Wired 802.1x NAC using CPPM with Azure AD over LLDP or using EAP-PEAP or EAP-TLS?
Hi Umair,
What do you mean with Azure AD over LLDP, I assume you think about Azure AD over LDAP?
If so, you can simply use any wired NAC Guide for ClearPass. Like this one:
https://support.hpe.com/hpesc/public/docDisplay?docId=a00091135en_us
There is nothing special with this.
In the latest ClearPass version, 6.12, you can even use AzureAD (which is now EntraID) directly, without LDAP. I haven’t tried so far but will for sure in the future.
BR
Florian
Hi Florian,
Thanks for your prompt response. Yes it was LDAP. I wanted to know if we can use Azure AD as an authentication source.
Hi Umair,
you can’t use AzureAD (EntraID) as an authentication source directly. You would need to onboard the devices first. Either using some internal tool, like Intune or ClearPass Onboarding. This will configure a certificate on the device. During authentication, the device will use this certificate to authenticate. ClearPass will check if the certificate is valid and allow access. With the latest version (6.12) you can also check some EntraID information during this process, like the group membership of the user to allow access based on that. Hope this helps.
BR
Florian
Hi Florian,
Thank you very much for your response. It is really helpful and I appreciate it.
Regards,
Umair
Hi Umair,
you’re welcome 🙂
BR
Florian
Hello
I very imprest for this articul. Maybe Do you have the same website for guest account (Azure AD ?
Hi Adam,
No, I do not have something like this currently. I’m working on an article for Onboarding, using Google Workspace. The Guest Workflow should be similar. I hope I can publish the article by the end of october.
BR
Florian
This article is really good.May i know what are the possible options for tacacs authentication whre Azure AD as aidentity source?
Hi,
Thanks for the feedback. Much appreciated.
Natively, Azure AD does not support any password based authentication which does not use the azure portal. So something like MS-Chap or PEAP is not supported anymore with azure AD. And Tacacs also belongs to those password based which are not supported anymore.
The only option to bring those back is to use an on-prem AD which is synched with Azure or to run this in the cloud like the azure ad services.
You would add those source as traditional AD sources and they will support password based authentications again.
That’s the only option I’m aware of.
BR
Florian
Hi Floria,
I have followed your guide and have things mostly working to authenticate users with Entra authentication, thanks so much. Question for you – I’m trying to assign a different VLAN to users based on group membership etc. I have this working in Clearpass already without using Guest/Captive Portal. Our APs are managed by Aruba Central. If I pass an attribute like “Aruba-User-Role” = test, I’ve created a role in Central called ‘test’ and have it set to use a specific VLAN however it’s not working. Not sure what I might be missing, I’m curious if you have done anything similar in the past or have any suggestions to try?
Hi Derek,
thanks for your comment. Much appreciated.
Regarding your question, I always recommend to send not only the role, but also the VLAN with the role to AP’s. For some reason, they do not always honor the VLAN configured in the role. It will also give you the flexibility to have the same role in different VLAN’s. Try sending “Aruba-Named-User-Vlan” with the VLAN name as together with the role. This should do the job.
BR
Florian