In this post, I describe how I use an Aruba Instant AP for tunnel all my traffic to my controller at home. This IAP VPN is very helpful when I need to show some lab scenarios. But you can also use it as your secure connection from a small branch office to the headquarter. Sure, you could use a RAP (Remote AP) and I used this setup in the past very successful, but the IAP solution scales much better.
You can have just a limited number of RAP’s in one location. But you can have up to 128 IAP’s per location. Whenever you need more than 4 RAP’s, consider the IAP VPN solution as well.
In the setup below, I use central for management. But you can also use AirWave or no management and configure the IAP’s manually, as well, to get the same results.
IAP VPN – Basic Setup
Normally, you send the wireless user in an IAP solution in a VLAN. But sometimes you need a central breakout for the users. This is possible with the IAP VPN solution. All you need is a controller, or for redundancy two controllers, at the central breakout point. The IAP create an IPSec tunnel to this controller. You can use this tunnel to send user traffic to the controller. The controller can now handle the traffic and send it to a VLAN at the central site.
The setup is very simple and easy. I start with the controller part. and afterward with the IAP part in central.
I run ArubaOS 8 on the controller:
show version
Aruba Operating System Software.
ArubaOS (MODEL: Aruba7005), Version 8.2.1.0
Website: http://www.arubanetworks.com
(c) Copyright 2018 Hewlett Packard Enterprise Development LP.
Compiled on 2018-03-16 at 17:27:35 UTC (build 64044) by p4build
ROM: System Bootstrap, Version CPBoot 1.0.2.0 (build 46859)
Built: 2014-10-31 10:10:57
Built by: p4build@re_client_46859
Switch uptime is 4 days 4 hours 21 minutes 8 seconds
Reboot Cause: POE Power Cycle (Intent:cause:register ee:ee:0:c)
Supervisor Card
Processor (XLP208 Rev B0 (Secure Boot) , 500 MHz) with 3797M bytes of memory.
32K bytes of non-volatile configuration memory.
1920M bytes of Supervisor Card system flash.The first step is to allow the IAP on the controller. This is the same as with all other AP’s. You need to whitelist the IAP. I use whitelist auth with ClearPass. Here you can check, how to use ClearPass for whitelist sync:
ArubaOS Controller Whitelist Sync with ClearPass
You have to use the remote AP whitelist for the IAP’s. And If you use ClearPass or any other radius server you can also specify the role for the IAP. Below is the summary screen of my enforcement profile for any IAP authentication:
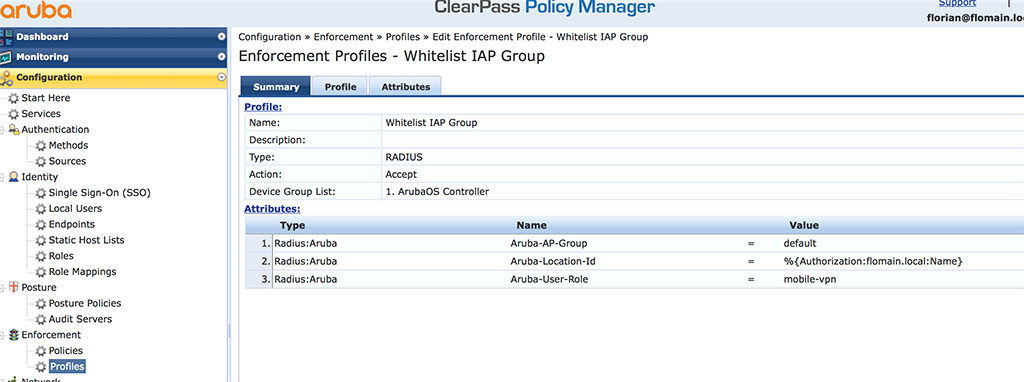
I use the default group, for the group assignment. You can use a different one, but keep in mind, the group doesn’t madders in this setup, as the controller did not apply any configuration for the IAP. Important is the “Aruba-Location-Id” to assign the correct IAP name on the controller. This makes troubleshooting much easier, later on. The role is not needed, as the controller has a default role for the IAP’s. If you would like to change it, you can send the role attribute as well.
The last step on the controller is to create an IP pool, for the inner tunnel IP’s. Either use the CLI and use this command:
ip local pool "mobile-iap" 10.193.168.2 10.193.168.254Or you can do the same in the GUI. Go to “Configuration–>Services–>VPN” and go down to “General VPN”. To create a new “Address Pool”, click the “+” sign:
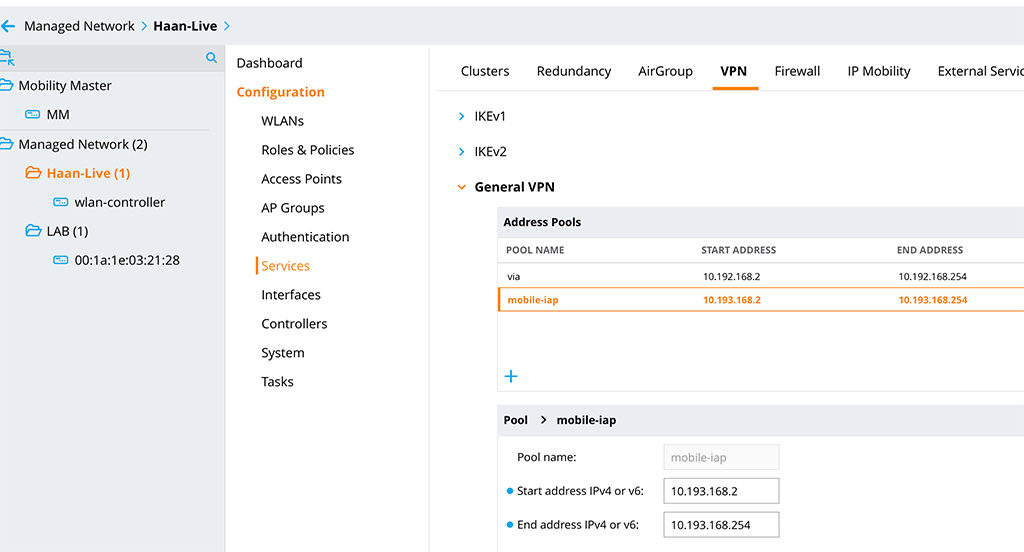
From this “Address Pool”, the IAP gets an inner tunnel IP address. You can either create a NAT rule for this address range or, which is my recommendation, use OSPF to distribute the routes in your environment. If you need help with OSPF on the Aruba controller, leave me a comment and I will help you, or write a post about it.
That is the controller part.
IAP VPN – IAP Part
I will show the setup with Aruba Central, but the configuration is the same for AirWave or the Instant GUI.
To start the configuration go to “Wireless Management–>VPN”:
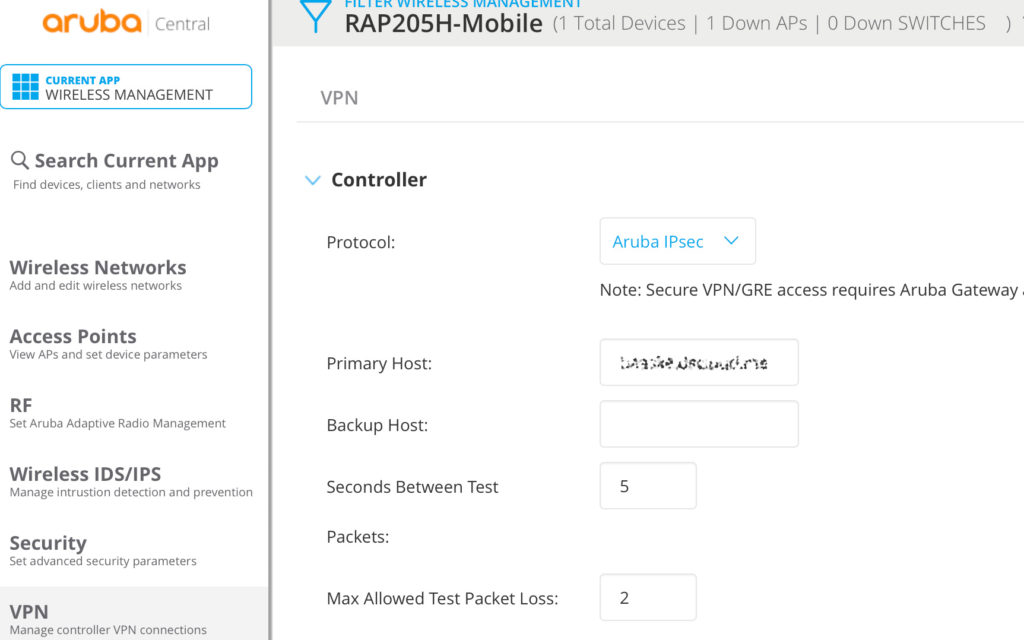
Replace the “Primary Host” and the “Backup Host” with your hostnames or IP addresses and make sure, you select “Aruba IPsec as the “Protocol”.
This creates a tunnel from the virtual controller of the IAP cluster to the Aruba controller. You can also select “Aruba GRE” for the “Protocol”. With “Aruba GRE”, you can build tunnels from every IAP in the cluster to the controller. This is very handy when you cannot use VLAN Tags between the IAP’s. The configuration would look like this:
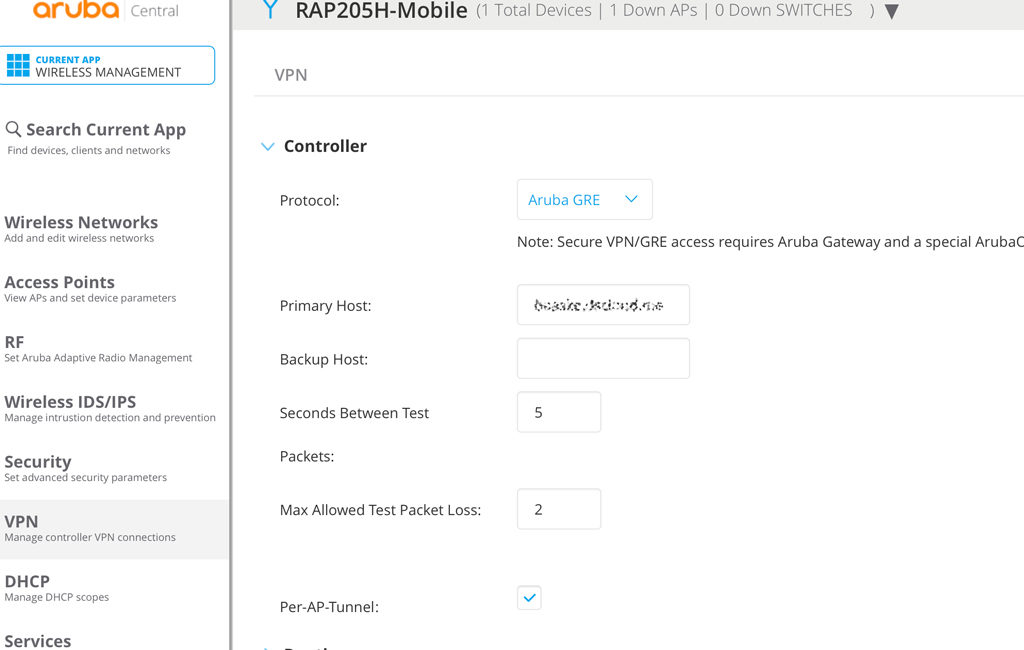
This creates a VPN tunnel from every IAP to the controller. This makes sense when you are not able to work with VLAN tags between the IAP cluster notes.
You can also configure “L2TPv3” and “Manual GRE”. But I have never used them in the past.
To allow the IAP, to reach internal resources as well, you can configure “Routing”. This is just below the configuration from above:
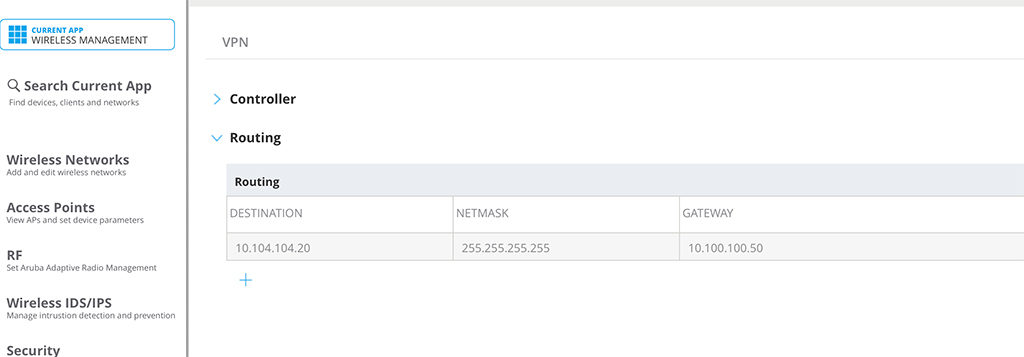
You can configure hosts or subnets to be available behind the tunnel. The important part is, that you need to configure the controller IP (the one, the IAP is connected to) as the gateway.
IAP VPN – Show Commands
You can check if the VPN is up and running from the CLI. First, let’s check the controller part. There is an ISAKMP entry for the IAP:
(wlan-controller) #show crypto isakmp sa
ISAKMP SA Active Session Information
------------------------------------
Initiator IP Responder IP Flags Start Time Private IP
------------ ------------ ----- --------------- ----------
10.100.100.50 10.100.100.70 i-v2-p Jul 3 02:19:33 -
10.106.106.10 10.100.100.50 r-v2-c-C Jul 3 04:37:59 10.106.106.10
10.106.106.11 10.100.100.50 r-v2-c-C Jul 3 04:53:29 10.106.106.11
137.226.133.33 10.100.100.50 r-v2-c-I Jul 3 09:58:35 10.99.99.10
Flags: i = Initiator; r = Responder
m = Main Mode; a = Agressive Mode; v2 = IKEv2
p = Pre-shared key; c = Certificate/RSA Signature; e = ECDSA Signature
x = XAuth Enabled; y = Mode-Config Enabled; E = EAP Enabled
3 = 3rd party AP; C = Campus AP; R = RAP; Ru = Custom Certificate RAP; I = IAP
V = VIA; S = VIA over TCP
Total ISAKMP SAs: 4The last entry is the IAP. It is the VC. I use the Aruba IPSec option for the VPN. There is also an IPSec SA entry:
(wlan-controller) #show crypto ipsec sa
IPSEC SA (V2) Active Session Information
-----------------------------------
Initiator IP Responder IP SPI(IN/OUT) Flags Start Time Inner IP
------------ ------------ ---------------- ----- --------------- --------
137.226.133.33 10.100.100.50 ae840700/47eaac00 UT2 Jul 3 09:58:34 10.99.99.10
10.100.100.50 10.100.100.70 9ed8e900/f4c43400 UT2 Jul 3 09:53:35 -
10.106.106.11 10.100.100.50 81b8a900/fa64ed00 UT2 Jul 3 08:34:58 10.106.106.11
10.106.106.10 10.100.100.50 756f1b00/20537e00 UT2 Jul 3 09:50:45 10.106.106.10
Flags: T = Tunnel Mode; E = Transport Mode; U = UDP Encap
L = L2TP Tunnel; N = Nortel Client; C = Client; 2 = IKEv2
Total IPSEC SAs: 4This time, it is the first entry. If both entries are present, you have the IAP in the IAP table as well:
(wlan-controller) #show iap table long
Trusted Branch Validation: Enabled
IAP Branch Table
----------------
Name VC MAC Address Status Inner IP Assigned Subnet Assigned Vlan Key Bid(Subnet Name) Tunnel End Points
---- -------------- ------ -------- --------------- ------------- --- ---------------- -----------------
ELAB-VC-001 b4:5d:50:c1:ef:fc UP 10.99.99.10 d80c02fb01ab73336419c72095819606e430511260f2fecfa4
Total No of UP Branches : 1
Total No of DOWN Branches : 0
Total No of Branches : 1Now, from the IAP:
ELAB-AP-003# show vpn status
profile name:default
--------------------------------------------------
current using tunnel :primary tunnel
current tunnel using time :8 minutes 57 seconds
ipsec is preempt status :disable
ipsec is fast failover status :disable
ipsec hold on period :600s
ipsec tunnel monitor frequency (seconds/packet) :5
ipsec tunnel monitor timeout by lost packet cnt :6
ipsec primary tunnel crypto type :Cert
ipsec primary tunnel peer address :controller-fqdn.tld
ipsec primary tunnel peer tunnel ip :10.100.100.50
ipsec primary tunnel ap tunnel ip :10.99.99.10
ipsec primary tunnel using interface :tun0
ipsec primary tunnel using MTU :1230
ipsec primary tunnel current sm status :Up
ipsec primary tunnel tunnel status :Up
ipsec primary tunnel tunnel retry times :1
ipsec primary tunnel tunnel uptime :8 minutes 57 seconds
ipsec backup tunnel crypto type :Cert
ipsec backup tunnel peer address :N/A
ipsec backup tunnel peer tunnel ip :N/A
ipsec backup tunnel ap tunnel ip :N/A
ipsec backup tunnel using interface :N/A
ipsec backup tunnel using MTU :N/A
ipsec backup tunnel current sm status :Init
ipsec backup tunnel tunnel status :Down
ipsec backup tunnel tunnel retry times :0
ipsec backup tunnel tunnel uptime :0From the output above, you can see, that the primary tunnel is up.
ELAB-AP-003# show vpn tunnels
Tunnel Flags: M = Master IAP; S = Slave IAP; P = Primary Tunnel
B = Backup Tunnel; R = Registered; H = Heartbeat Enable
Tunnel Info for peer address 10.100.100.50
--------------------------------------------
Type Value
---- -----
Source IP 10.99.99.10
Destination IP 10.100.100.50
End IP 84.153.110.129
Default GW 192.168.0.254
Use count 1
Ifindex 17
Ifname tun0
Flags MPRH
Retry count for Register Request 0
Last Heartbeat 15998
Heartbeat Encap/Decap 108(seq 108)/109(seq 108)
GRE Encap/Decap 1582/1581
For DHCP Profile ELAB-Management
Retry count for Vlan Add Request 0
Old Subnet Status Normal
Existing Subnet Status NormalOn a slave IAP it looks like this:
ELAB-AP-001# show vpn status
profile name:default
--------------------------------------------------
current using tunnel :unselected tunnel
current tunnel using time :0
ipsec is preempt status :disable
ipsec is fast failover status :disable
ipsec hold on period :600s
ipsec tunnel monitor frequency (seconds/packet) :5
ipsec tunnel monitor timeout by lost packet cnt :6
ipsec primary tunnel crypto type :Cert
ipsec primary tunnel peer address :N/A
ipsec primary tunnel peer tunnel ip :N/A
ipsec primary tunnel ap tunnel ip :N/A
ipsec primary tunnel using interface :N/A
ipsec primary tunnel using MTU :N/A
ipsec primary tunnel current sm status :Init
ipsec primary tunnel tunnel status :Down
ipsec primary tunnel tunnel retry times :0
ipsec primary tunnel tunnel uptime :0
ipsec backup tunnel crypto type :Cert
ipsec backup tunnel peer address :N/A
ipsec backup tunnel peer tunnel ip :N/A
ipsec backup tunnel ap tunnel ip :N/A
ipsec backup tunnel using interface :N/A
ipsec backup tunnel using MTU :N/A
ipsec backup tunnel current sm status :Init
ipsec backup tunnel tunnel status :Down
ipsec backup tunnel tunnel retry times :0
ipsec backup tunnel tunnel uptime :0
ELAB-AP-001# show vpn tunnels
Tunnel Flags: M = Master IAP; S = Slave IAP; P = Primary Tunnel
B = Backup Tunnel; R = Registered; H = Heartbeat Enable
Tunnel Info for peer address 10.100.100.50
--------------------------------------------
Type Value
---- -----
Source IP 10.99.99.10
Destination IP 10.100.100.50
End IP 84.153.110.129
Default GW 0.0.0.0
Use count 0
Ifindex 0
Ifname Null
Flags SP
Retry count for Register Request 0
GRE Encap/Decap 0/0
For DHCP Profile ELAB-Management
Retry count for Vlan Add Request 0
Old Subnet Status Normal
Existing Subnet Status NormalNow, let’s change the VPN type to Aruba GRE. I also enable “Per -AP-Tunnel”.
The first two commands look the same. There is one IPSec tunnel from the VC to the controller. But the last output from the controller is different:
(wlan-controller) #show iap table long
Trusted Branch Validation: Enabled
IAP Branch Table
----------------
Name VC MAC Address Status Inner IP Assigned Subnet Assigned Vlan Key Bid(Subnet Name) Tunnel End Points
---- -------------- ------ -------- --------------- ------------- --- ---------------- -----------------
ELAB-VC-001 b4:5d:50:c1:ef:fc UP 10.99.99.10 d80c02fb01ab73336419c72095819606e430511260f2fecfa4 192.168.0.180,192.168.0.183,192.168.0.182,192.168.0.181
Total No of UP Branches : 1
Total No of DOWN Branches : 0
Total No of Branches : 1As you see from the output above, the controller list all the IAP’s in the IAP cluster as well.
The IAP output is different as well. The VC has one IPSec tunnel active:
ELAB-AP-003# show vpn status
profile name:default
--------------------------------------------------
current using tunnel :primary tunnel
current tunnel using time :17 minutes 39 seconds
ipsec is preempt status :disable
ipsec is fast failover status :disable
ipsec hold on period :600s
ipsec tunnel monitor frequency (seconds/packet) :5
ipsec tunnel monitor timeout by lost packet cnt :6
ipsec primary tunnel crypto type :Cert
ipsec primary tunnel peer address :controller-fqdn.tld
ipsec primary tunnel peer tunnel ip :10.100.100.50
ipsec primary tunnel ap tunnel ip :10.99.99.10
ipsec primary tunnel using interface :tun0
ipsec primary tunnel using MTU :1230
ipsec primary tunnel current sm status :Up
ipsec primary tunnel tunnel status :Up
ipsec primary tunnel tunnel retry times :1
ipsec primary tunnel tunnel uptime :17 minutes 39 seconds
ipsec backup tunnel crypto type :Cert
ipsec backup tunnel peer address :N/A
ipsec backup tunnel peer tunnel ip :N/A
ipsec backup tunnel ap tunnel ip :N/A
ipsec backup tunnel using interface :N/A
ipsec backup tunnel using MTU :N/A
ipsec backup tunnel current sm status :Init
ipsec backup tunnel tunnel status :Down
ipsec backup tunnel tunnel retry times :0
ipsec backup tunnel tunnel uptime :0And through the IPSec tunnel, the IAP has a GRE tunnel:
ELAB-AP-003# show vpn tunnels
Tunnel Flags: M = Master IAP; S = Slave IAP; P = Primary Tunnel
B = Backup Tunnel; R = Registered; H = Heartbeat Enable
Tunnel Info for peer address 10.100.100.50
--------------------------------------------
Type Value
---- -----
Source IP 10.99.99.10
Destination IP 10.100.100.50
End IP 84.153.110.129
Default GW 192.168.0.254
Use count 1
Ifindex 17
Ifname tun0
Flags MPRH
Retry count for Register Request 0
Last Heartbeat 15529
Heartbeat Encap/Decap 496(seq 496)/496(seq 496)
GRE Encap/Decap 1114/1113
For DHCP Profile ELAB-Management
Retry count for Vlan Add Request 0
Old Subnet Status Normal
Existing Subnet Status NormalFrom a slave IAP it looks like this:
ELAB-AP-001# show vpn status
profile name:default
--------------------------------------------------
current using tunnel :unselected tunnel
current tunnel using time :0
ipsec is preempt status :disable
ipsec is fast failover status :disable
ipsec hold on period :600s
ipsec tunnel monitor frequency (seconds/packet) :5
ipsec tunnel monitor timeout by lost packet cnt :6
ipsec primary tunnel crypto type :Cert
ipsec primary tunnel peer address :N/A
ipsec primary tunnel peer tunnel ip :N/A
ipsec primary tunnel ap tunnel ip :N/A
ipsec primary tunnel using interface :N/A
ipsec primary tunnel using MTU :N/A
ipsec primary tunnel current sm status :Init
ipsec primary tunnel tunnel status :Down
ipsec primary tunnel tunnel retry times :0
ipsec primary tunnel tunnel uptime :0
ipsec backup tunnel crypto type :Cert
ipsec backup tunnel peer address :N/A
ipsec backup tunnel peer tunnel ip :N/A
ipsec backup tunnel ap tunnel ip :N/A
ipsec backup tunnel using interface :N/A
ipsec backup tunnel using MTU :N/A
ipsec backup tunnel current sm status :Init
ipsec backup tunnel tunnel status :Down
ipsec backup tunnel tunnel retry times :0
ipsec backup tunnel tunnel uptime :0
ELAB-AP-001# show vpn tunnels
Tunnel Flags: M = Master IAP; S = Slave IAP; P = Primary Tunnel
B = Backup Tunnel; R = Registered; H = Heartbeat Enable
Tunnel Info for peer address 10.100.100.50
--------------------------------------------
Type Value
---- -----
Source IP 10.99.99.10
Destination IP 10.100.100.50
End IP 84.153.110.129
Default GW 0.0.0.0
Use count 0
Ifindex 0
Ifname Null
Flags SP
Retry count for Register Request 0
GRE Encap/Decap 0/0
For DHCP Profile ELAB-Management
Retry count for Vlan Add Request 0
Old Subnet Status Normal
Existing Subnet Status NormalThere is no VPN active. But there is a GRE tunnel (the lower output). This GRE tunnel uses the IPSec tunnel from the VC as well. This allows the GRE tunnel to work even in an environment with NAT devices between the IAP and the controller. Isn’t this a great feature?
You have now the connection between the IAP and the central controller. All the different options, to use this connection will come in one of the next posts.
If you find this post interesting, leave me a comment and share it with your friends. If you don’t like the post, leave me a comment and share it with your enemy. But whatever you do, leave me a comment, now.
As always, great article Florian. Thx!
Hello Florian! Great explanation! I am running this setup on a 6.5 controller and migrated to a MM/MD setup, where I designated a controller for RAPNG operations. I could deploy IPsec to the controller and can reach the IAPs through VPN (from even a DC computer) but the show iap table remains empty. This causes a problem, since the tunneled VLANs are not going through the Ipsec tunnel. I was thinking there might be a version issue on the IAP side (6.5.4.12) and I am running 8.5.0.9 on MD side. Can you tell me which version and model of IAP you are/were using? Thanks in advance!
Hi Daniel,
with 8.4 there was a change to the way IAP VPN works with the controller. If have all (IAP + Controller) >= 8.4 it works. If both are < 8.4 it works as well. But in your situation, the controller is 8.5.0.9 (which is above 8.4) and your IAP's are on 6.5.4.12 (which is way below 8.4). To make this work again you need the compatibility mode here: https://www.arubanetworks.com/techdocs/ArubaOS_86_Web_Help/Content/arubaos-solutions/iap-vpn-supp/back-comp.htm
Hope this helps to solve your issue.
BR
Florian
Hello Florian, i have VPN-IP through internet and need NAT and IPSec. On the remote site i have a switch with no vlans (cant use it) and an instant cluster with 2x IAPs and a guest SSID. Centralized L2 DHCP and ClearPass centralized for Guest Portal. Can i make this work without creating any vlans on the switch ? How ?
The issue here is that i cant use GRE tunnels because of NAT and Internet.
Thanks.
Forian, just a quick editorial note
In the section “ArubaOS Controller Whitelist Sync with ClearPass” you have written
You have to use the remote AP whitelist for the IAP’s. And If you use ClearPass or any other radius server you can also psecify the role for the IAP. Below is the summary screen of my enforcement profile for any IAP authentication:
specify is misspelled in the second sentence.
Hi Matt,
thanks for the hint. I corrected that 🙂
BR
Florian
Hello, after central configures VPN for configuring IAP and successfully establishes IPSec with the controller, who will manage IAP? Will it be managed by the controller or continue to be managed by central. I can understand that for convenience, we first use central to deploy IAP VPN. Thank you.
报错 笔记
Hello Zhang,
The controller is only used for VPN termination, all configurations will stay within central.
BR
Florian