When you setup ClearPass, you always need to authenticate your operator. In this post, I will describe an easy way to use Active Directory for ClearPass operator login. I use AD here because most of my customers use AD. So, we can work with it and do not have to set up something new or use the admin database in ClearPass. This will only create a shadow database with separate passwords and a separate structure.
ClearPass Operator Login – Copy the Existing Service
ClearPass use itself for authentication as well. This means when you hit the login button on the ClearPass login page, ClearPass create a TACACS request and authenticate the user with a service. This service is the default “[Policy Manager Admin Network Login Service]”:
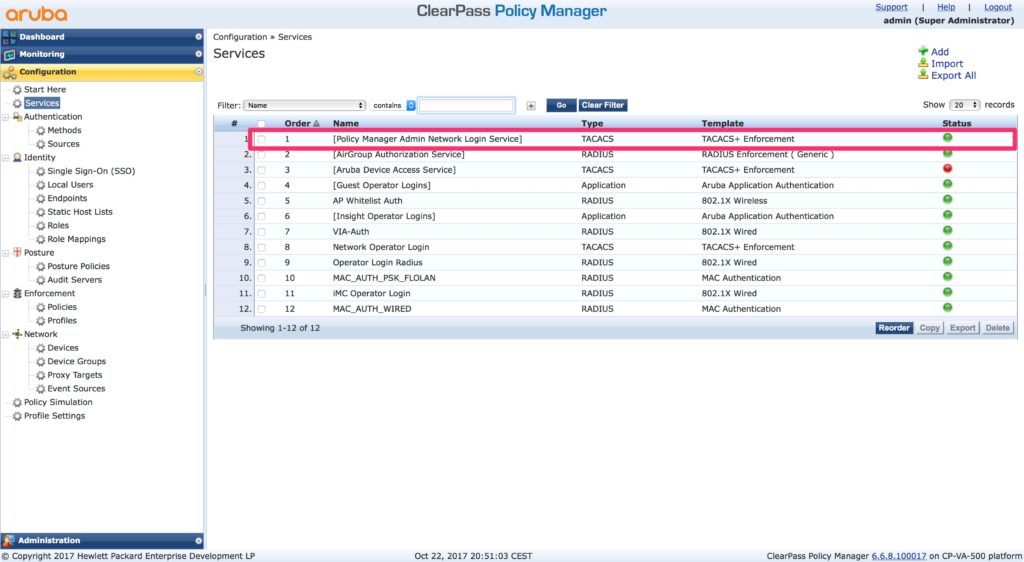
To remove or to disable this service make it impossible for ClearPass to authenticate the operator. So, the best option is to adjust the service to use AD as well. But, this is a default service and you cannot change it. The only option is to copy the service and modify the copy. To copy the service, select the service (check the checkmark at the beginning of the row) and hit the “Copy” button at the below the table. This creates a new service in the last row. Open this service to modify the service:
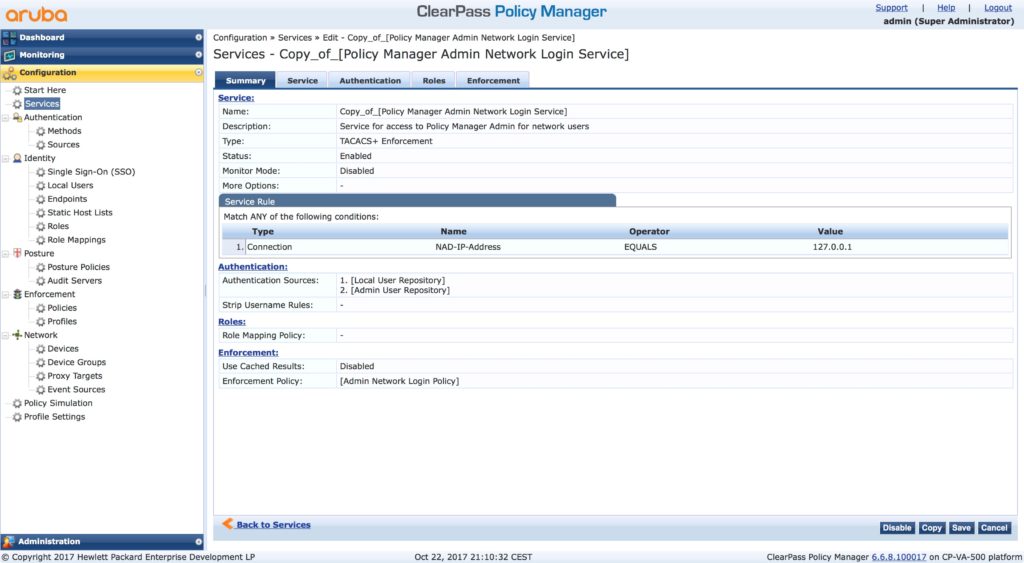
The service is the same as the original one. But we change this soon.
ClearPass Operator Login – Modify the Copy of the Default Service
Select the second tab, “Service” and change at least the name:
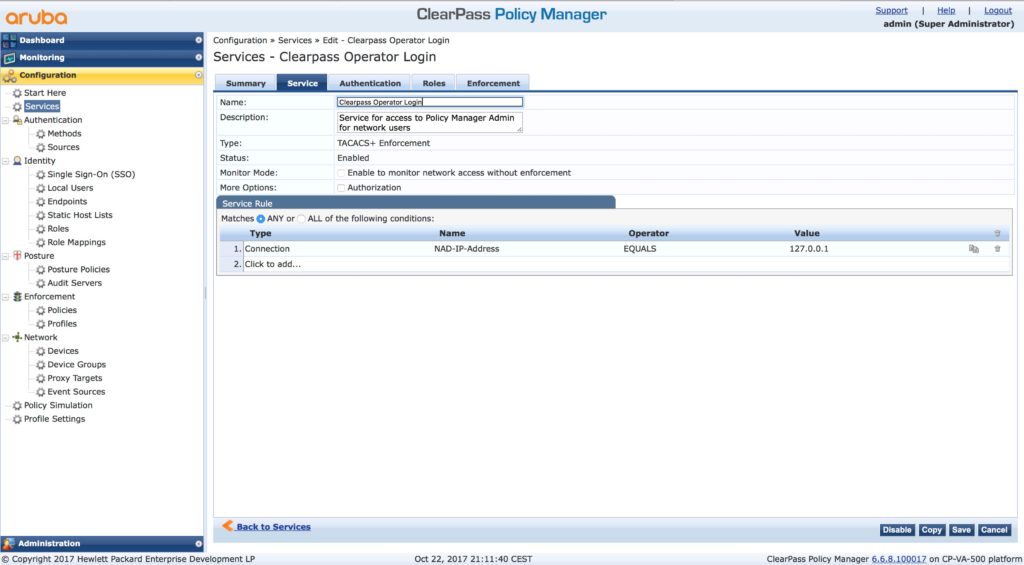
You can also change the description, but actually, the default description is pretty good.
Go to “Authentication”:
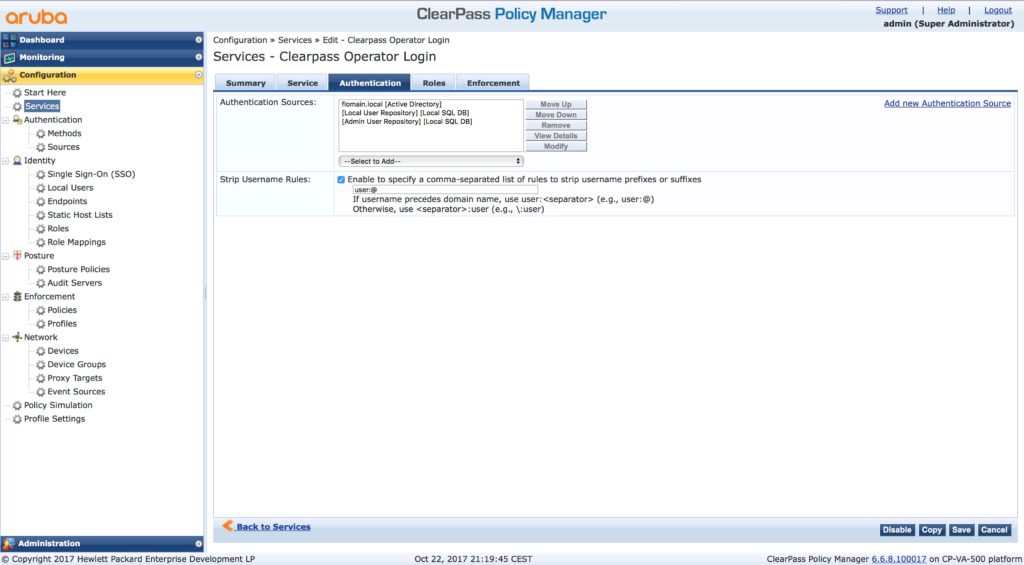
Add the AD to the list of “Authentication Sources”. I also set it to top of the list as this is my main repository for users. Leave the existing sources in the list.
My users use “[email protected]” as authentication name. To strip the “@domain.tld” from the name enable the “Strip Username Rules” and add “user:@”.
Go to the “Roles” tab:
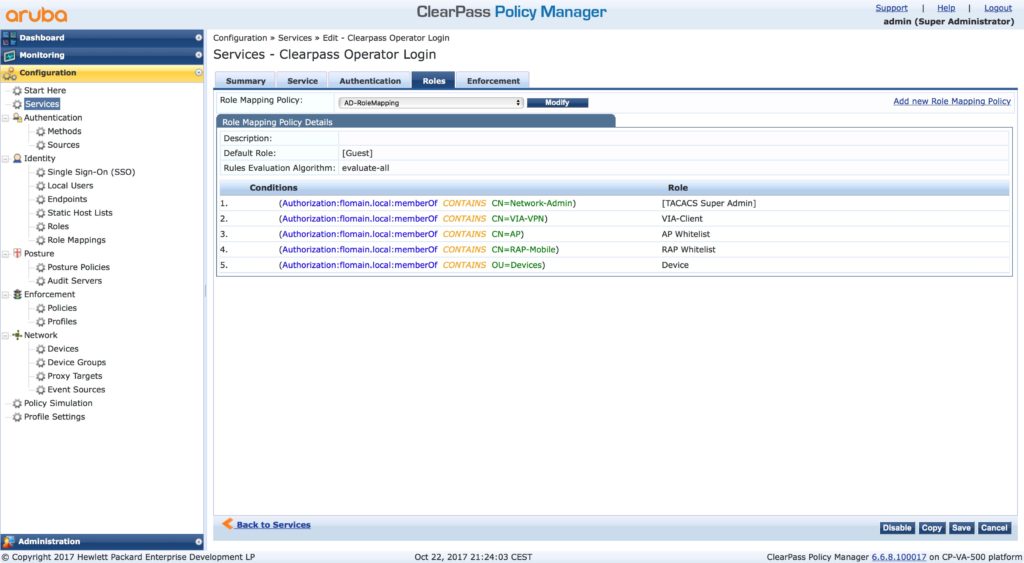
You do not have to use roles mapping. But it makes life easier if you do. I have a default role mapping profile. Every group in my active directory, which is used for authentication and/or authorization has a role in ClearPass. This role mapping profile maps the group from AD to a role in ClearPass. The benefit of role mapping comes on the next tab:
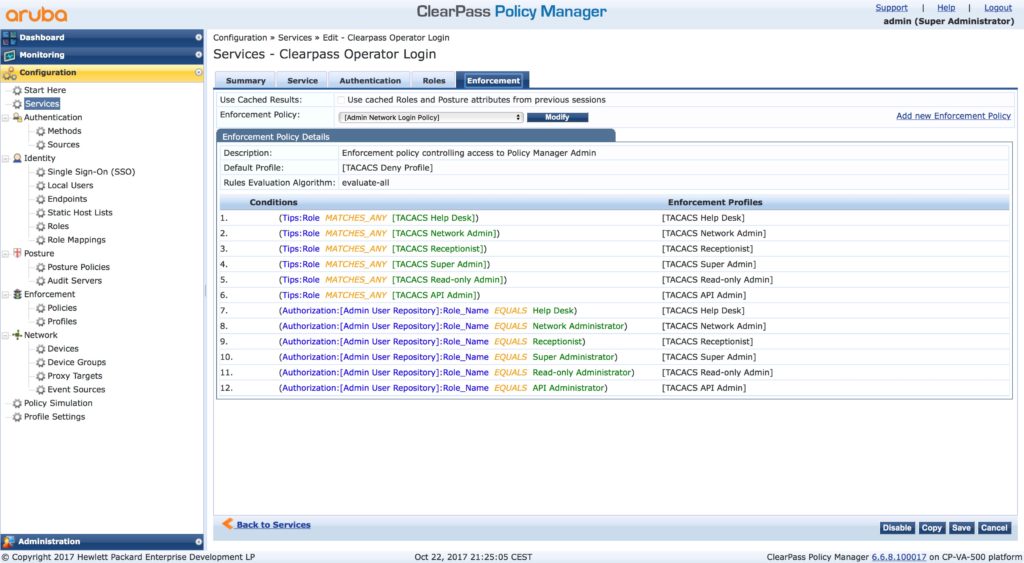
This is the default enforcement policy. There are many conditions for default roles. I simply match my AD groups to those roles and so I can use the “[Admin Network Login Policy]”. This saves me a lot of time. But, as always, you can, of course, create your own rules and policies. But remember, to have a fallback plan, include the conditions from above in your policy. This makes sure, you can use the local admin account in the condition of disaster. so, change the default password for the admin account to something safe and complicated and hide it somewhere.
ClearPass Operator Login – Activate the Service
To use the new service, you have to move it in front of the old one. Go back to the “Services” list and click the “Reorder” button:
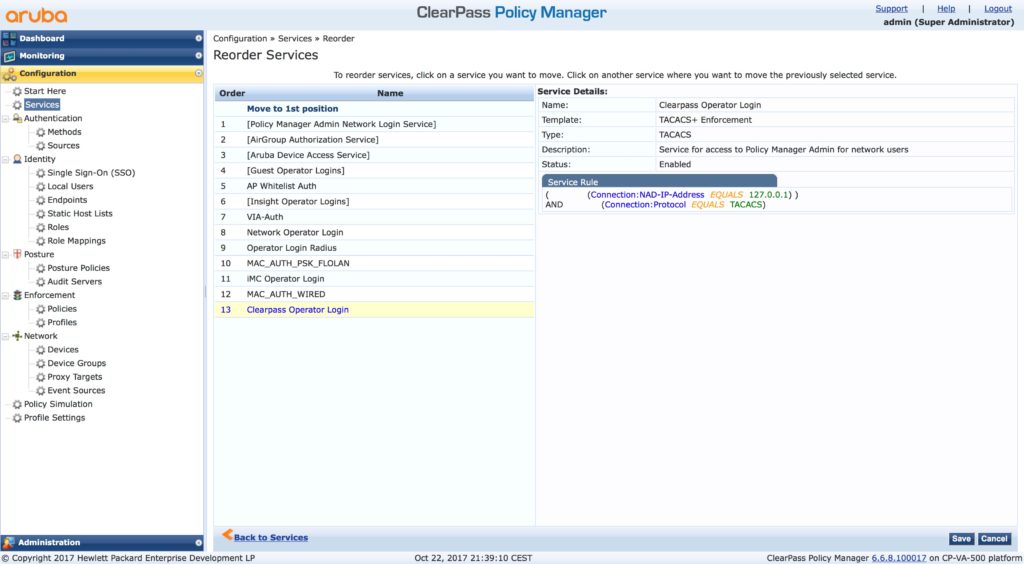
Move it to position one. And now, finger crossed that it works. Logout from ClearPass and use an AD account to log in again. To make it, even more secure, use a different browser to test the login without logging out before.
If you are in again, we did it correctly. You can now disable the old service. Just click the green light at the end of the row. It turns red.
Also, test the login with the built-in account, to make sure that the fall back plan is working.
If you find this post interesting, leave me a comment and share it with your friends. If you don’t like the post, leave me a comment and share it with your enemy. But whatever you do, leave me a comment, now.