This is the second post on the TACACS+ topic. This time the post is all about TACACS+ operator command authorization and accounting. This is very helpful for logging who does what at which time and makes troubleshooting easier. Operator command authorization and accounting means, that all commands issued at the device, are sent to the TACACS+ server for accounting and authorization. Only when the TACACS+ server permits the command, the operator can issue the command. If not he
Aruba-2930F-8G-PoEP-2SFPP# configure
Not authorized to run this commandIf you also follow my previous post here, you have ClearPass already configured and ready to also do command authorization and accounting. That’s why I will not cover the basic steps gain. If you feel, you need more details on the basics, have a look at the above-mentioned post.
Unfortunately, ArubaOS for wireless controller and AirWave do not support command authorization and accounting. Command authorization for those platforms is achieved by creating the respective role on the controller or on AirWave. Logging of executed commands is done with the normal logging facilities.
For the rest of this post, I cover operator authorization and accounting for Comware and ArubaOS for switches.
Operator Authorization and Accounting for Comware
Comware has very good build in operator authorization and accounting capabilities. The needed tasks are very simple. If you have followed my previous post, there are only small additions to the configuration.
The first step is to enable command authorization and accounting for incoming management connections:
line vty 0 63
authentication-mode scheme
user-role level-15
command authorization
command accountingThe last two commands are new. They enable authorization and accounting.
Afterward, update the domain, which is used to authenticate the management user:
domain cppm
authentication login hwtacacs-scheme cppm-tacacs
authorization login hwtacacs-scheme cppm-tacacs
accounting login hwtacacs-scheme cppm-tacacs
authorization command hwtacacs-scheme cppm-tacacs
accounting command hwtacacs-scheme cppm-tacacsThe last two lines are new. They enabling the domain to use the “cppm-tacacs” scheme to do command authorization and account as well. Save the configuration and head over to CearPass.
I reuse the profiles from my last post. I use a simple policy, to allow only “display this” and “display current-configuration” for demonstration purpose. Open the enforcement profile. Select the last tab, “Commands”:
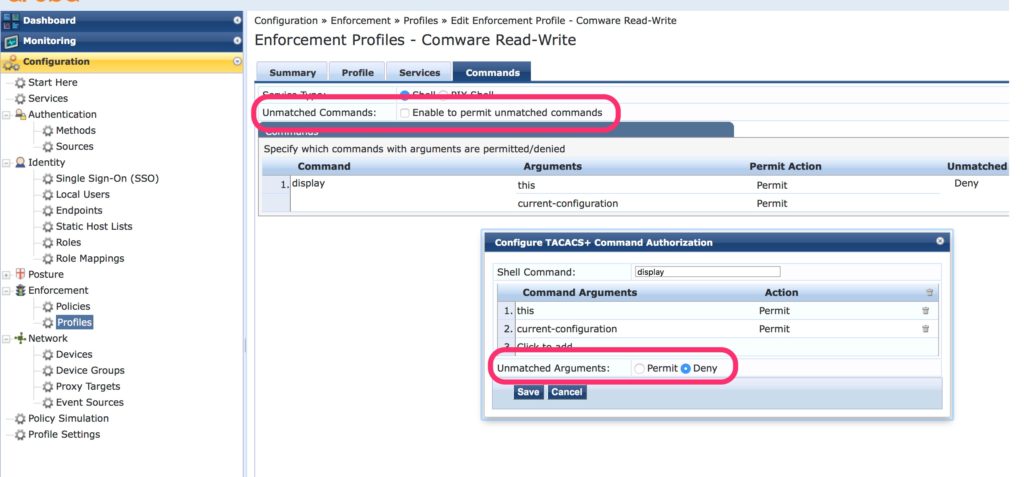
Make sure, that you disallow unmatched commands, the red squares. The rest is very simple. Here you can create a list of commands. The list defines if the command is permitted or denied. I create a simple rule to allow “display this” and “display current-configuration” but any other combination with the command “display” or any other command is not permitted.
You can see this in action in the monitoring section of ClearPass:
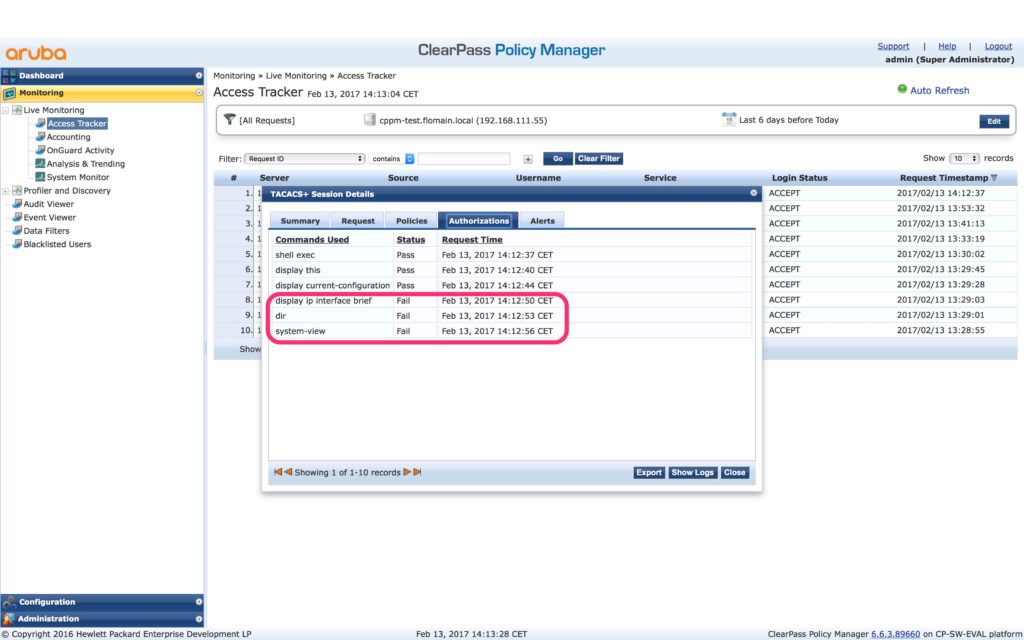
The above shows the output from the “Access Tracker”. You can see, which commands are allowed and which were refused. The benefit is, that with accounting only, you see only the allowed commands.
Operator Authorization and Accounting for ArubaOS Switches
ArubaOS switches have operator authorization and accounting support as well. The configuration is very simple. I assume the config is already configured for the basic TACACS+ authentication as in my previous post. To enable authorization for commands, use this command:
aaa authorization commands tacacsThis enables command authorization for every command issue on the switch. To enable only command authorization in manager level use this command:
aaa authorization commands access-level managerThe default is “all”.
The last step is to enable accounting. To enable command accounting use this command:
aaa accounting commands interim-update tacacsNow, head over to ClearPass and modify the profiles to allow or disallow commands:
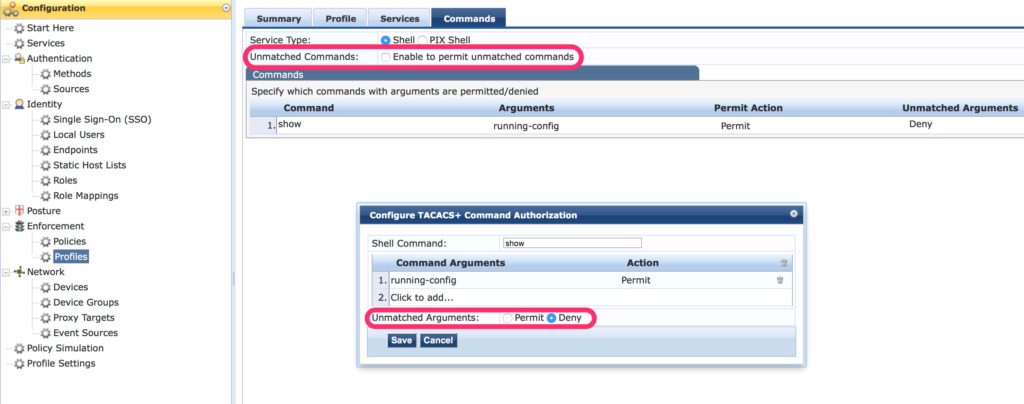
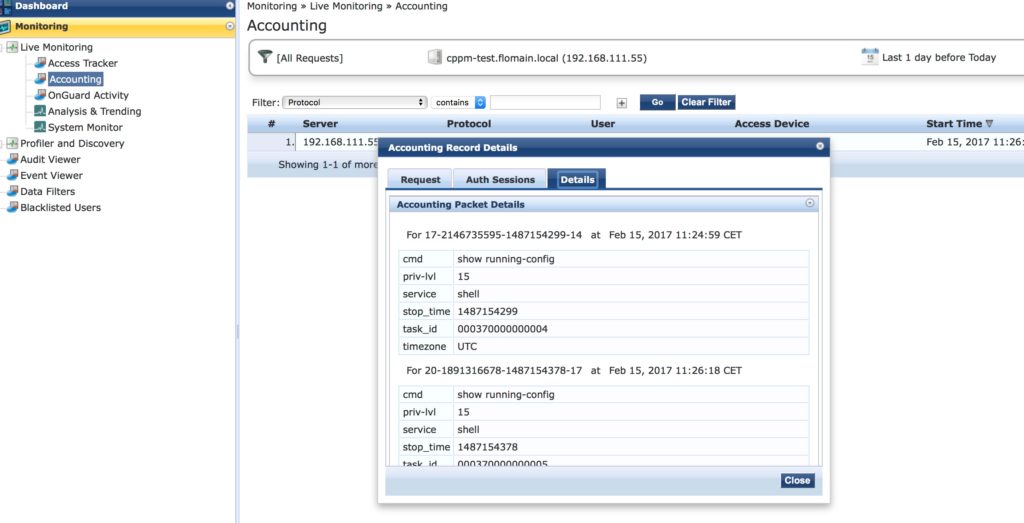
Again, I used the show command to make the example. This time, I allow the “show running-config” command. I deny all other commands:
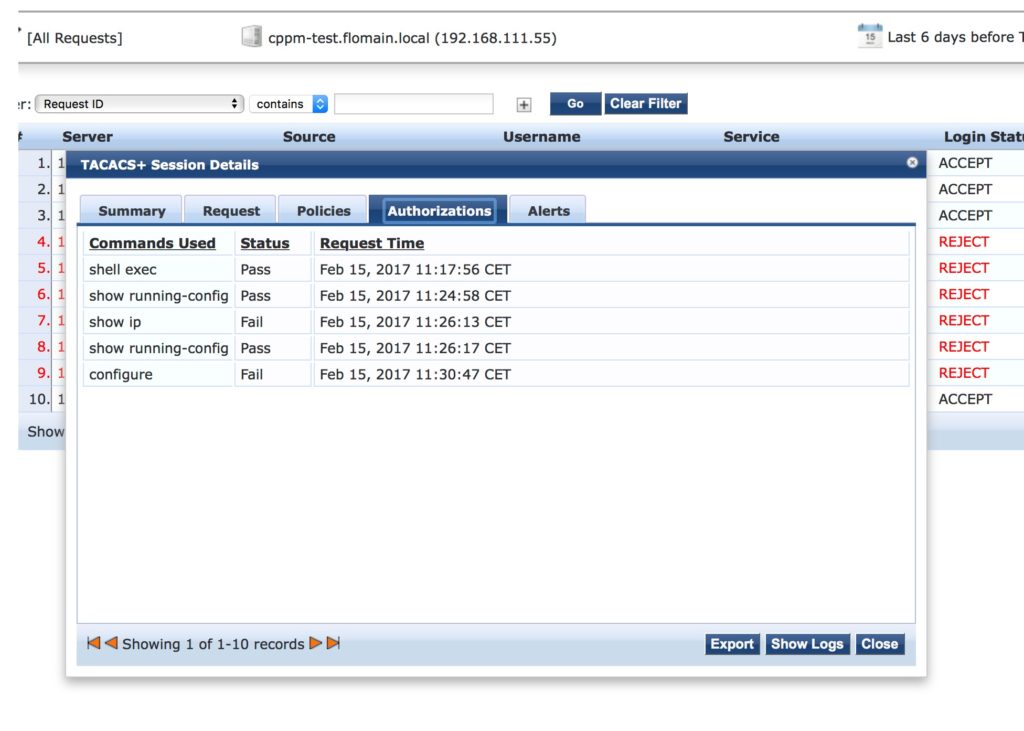
Accounting is working as well:
Following the above paragraph, you have configured operator authorization and accounting on ArubaOS switches.
For some ArubaOS switches, this is not possible. They support only TACACS+ authentication. I will describe this in the next post.
Feel free to write me your opinion below as a comment. I appreciate any discussion about the topic.